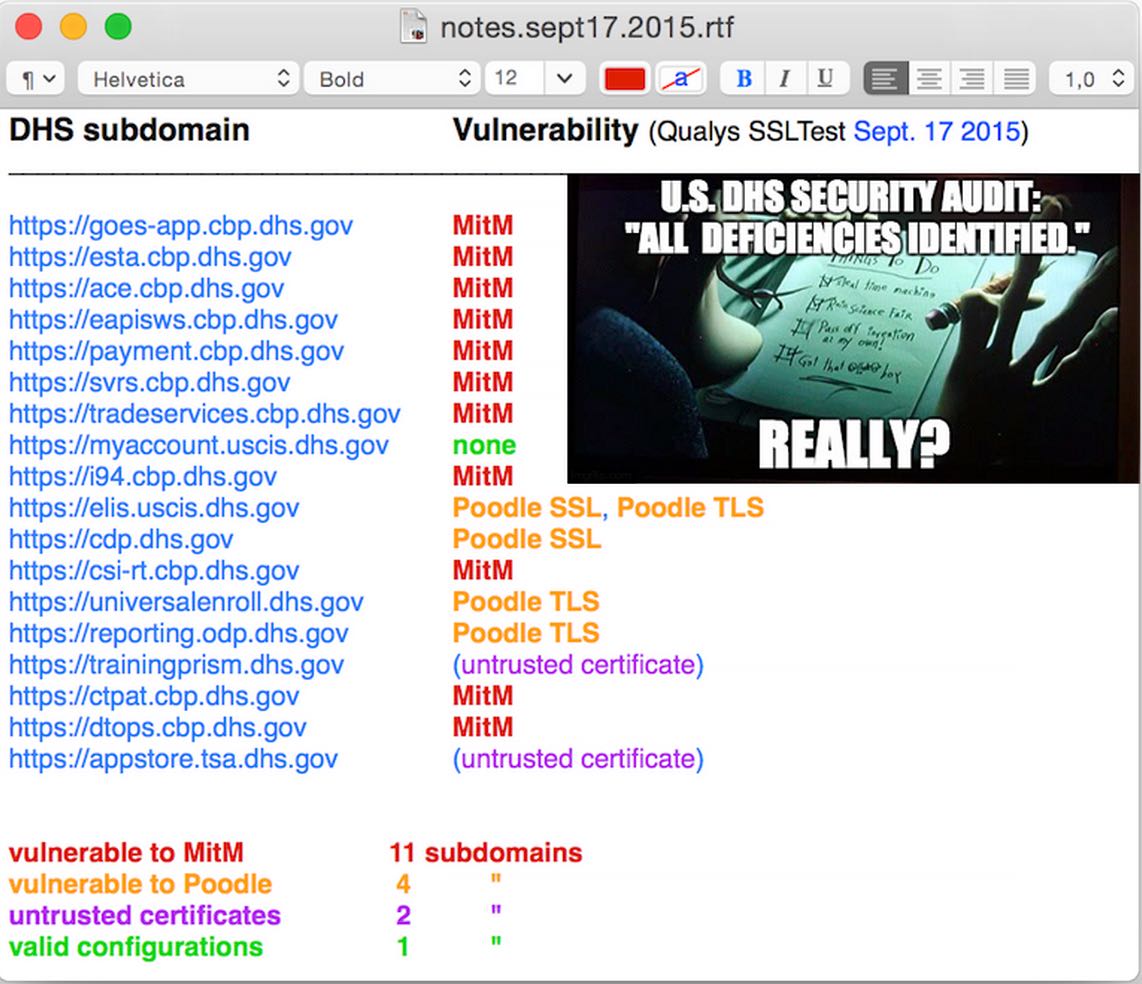
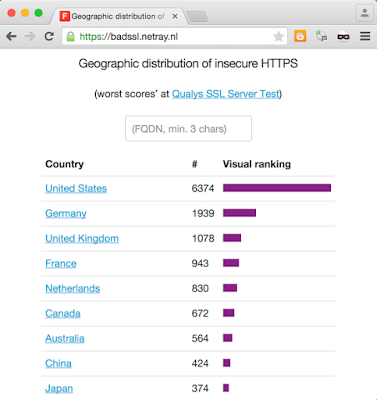
Is DHS running honeypots?
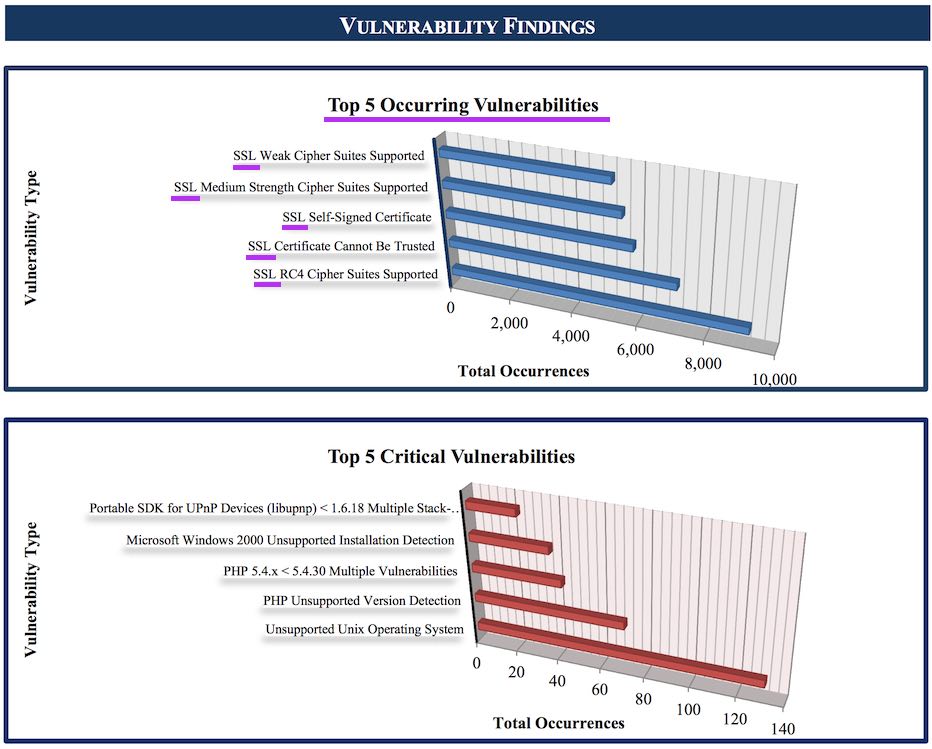
When in September 2015 DHS published its own Security Audit Report , I was rather speechless I could not find any mention of "SSL" or "TLS" in the text, but apparently DHS has been aware of Transport Layer Security earlier than that. Today KrebsOnSecurity published a post titled DHS Giving Firms Free Penetration Tests containing a link to a document which include the status update about the ongoing cyber programs and efforts underway at the Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC) . In a rather confusing timeline, we read first about a DHS ignoring SSL/TLS during its own Security Audit Report (Sept. 2015) and today about how SSL (TLS) related vulnerabilities occupy 5/5 of the Top 5 (Occurring) Vulnerabilities list in the DHS NCATS Year-Engagement Report 2014 (which indeed might have more conveniently be published at an earlier date). The reason for this post is not the confusing orde